Where Soft Skills Meet Generative AI
The rise of generative AI tools has ushered in a new era in modern businesses, bringing with it untapped potential as well as unprecedented challenges. This technology has exploded onto the scene, and there are no signs that it will be slowing down anytime soon. Some organizations have decided that
Leaning on Subject Matter Experts (When You Know Stuff Too)
Being boss doesn't mean you have all the answers, just the brains to recognize the right one when you hear it.” —Katherine Plumber.
Mastering the Initial Incident Meeting: Top Ten Tips for Effective Cybersecurity Incident Response
In the world of cybersecurity, large-scale incidents require a swift and coordinated response. When facing a significant security breach, the initial incident meeting is critical for gathering the right people, setting the tone, and establishing a clear plan of action. This article will explore the top ten things to do
The Power of Mentorship in Cybersecurity: Nurturing Growth, Continuous Learning, and Humility
I was fortunate that my first major job in cybersecurity had a strong mentor program. This was Cigital when it was still heavily focused on deeply technical application security services. We didn't have managers, not outside of a project. To help with career growth, it was all about
How Secure is Secure Enough?
Tl;dr: good practitioners should weigh “enough” security for both technical and business drivers.
Mastering Email Writing as a SOC Analyst: Tips and Best Practices for Cybersecurity Professionals
As a SOC analyst, you're responsible for monitoring and responding to security incidents in real-time. One of the key tools you'll use to communicate with your team and other stakeholders is email. But writing a good email as a SOC analyst is more than just getting
From Bits to Bias: Unveiling the Hidden Dangers of Toxic Cyber Cultures
On the Soft Side of Cyber, we've talked about what makes up a strong culture. This is also the final article in our short series on diversity, equity, and inclusion (DEI). We started this series with the different layers of diversity and the benefits of a diverse team.
Part 3: Fostering an Inclusive Workplace Culture for Cybersecurity Teams
Welcome back for the 3rd installment in our series about diversity, equity, and inclusion (DEI) in cybersecurity. In the first piece, we spoke about how diverse teams help advance cybersecurity. We discussed how a wider range of people and viewpoints aid in the detection and mitigation of novel security threats.
Vulnerability Cognition and Communication
This post was guest authored by Nikki Robinson. Vulnerability management is complex. It is, to be blunt, no fun at all. Especially in complex and complicated environments, vulnerability management can feel overwhelming. The sheer volume of vulnerabilities released daily into the National Vulnerability Database (NVD), the scores of vulnerabilities and
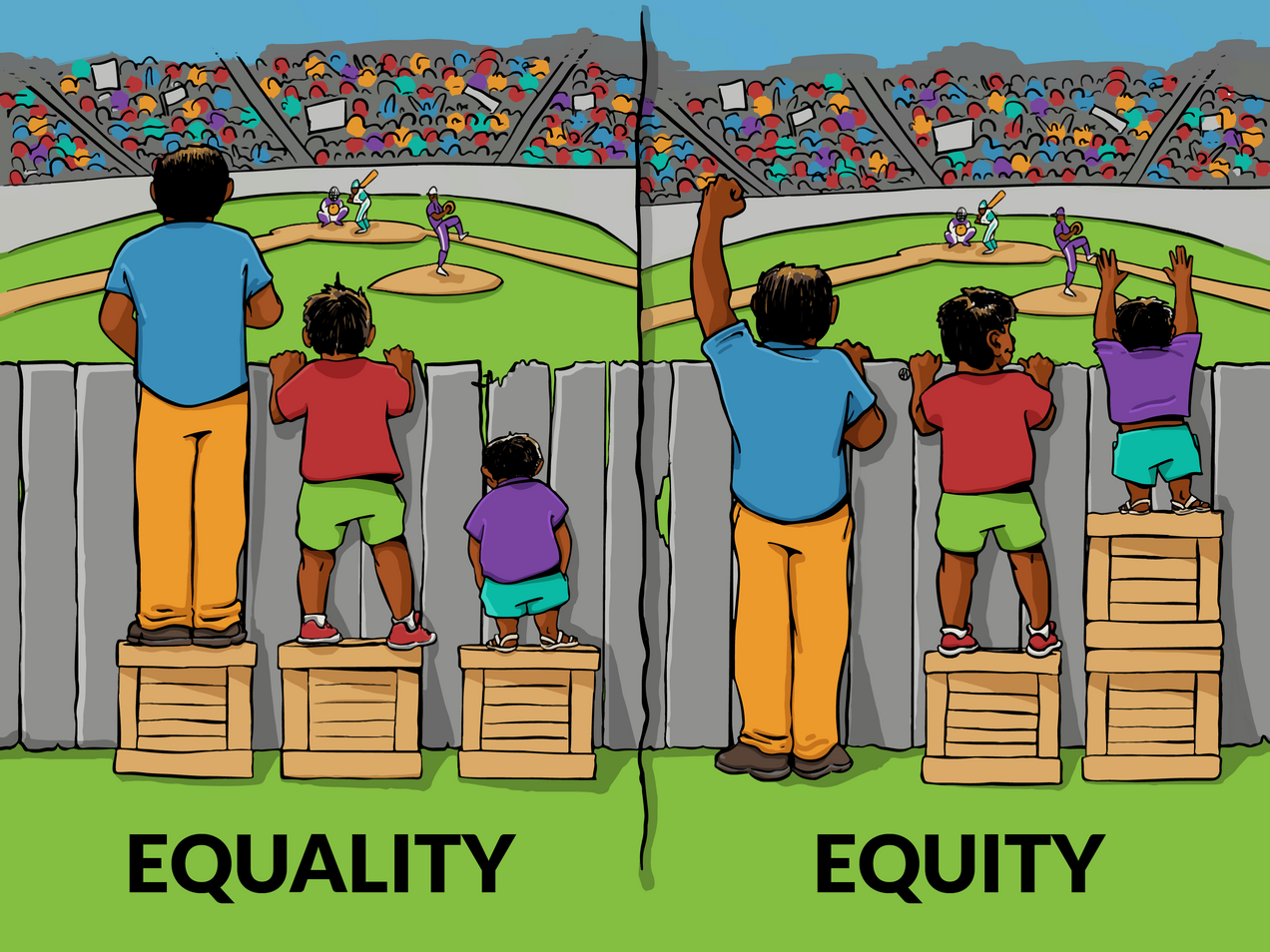
Part 2 - The Value of Equity in Cybersecurity Teams
Do you consider the team and environment in which you work to be fair? Fairness is the core of what it means to be equitable over equal. Things can be equal without being fair for everyone involved. In this article, I want to unpack this question and provide leaders and
Part 1 - Diversity in Cybersecurity: Strengthening the Industry Together
We here at Soft Side of Cyber are excited to share this new three-part series with you in which we'll go into the heart of diversity, equity, and inclusion (DEI) in the cybersecurity sector. Today, we'll begin the series by discussing the significance of diversity in
Bridging Tarot, Spirituality, and Cybersecurity
This article was a guest post from Caroline Wong. It's uncommon to see the words cybersecurity and tarot used together. So I will ask you to consider that perhaps the intersection exists in the minds of cybersecurity practitioners. Caroline, have you gone completely off the deep end? You